Learn extra at:
In a nutshell: A safety researcher lately uncovered almost three dozen Chrome Internet Retailer extensions exhibiting suspicious conduct. Many current themselves as search assistants, whereas others pose as advert blockers, safety instruments, or extension scanners – all mysteriously linked to a single, unused area.
John Tucker, founding father of browser safety agency Secure Annex, found the suspicious extensions whereas aiding a shopper who had put in a number of for safety monitoring. The primary crimson flag: two of the 132 extensions he analyzed had been unlisted, that means they do not seem in internet searches or the Chrome Internet Retailer. Customers can solely obtain these instruments by way of a direct URL. Unlisted extensions aren’t that unusual. Companies generally use them to restrict public entry to inner instruments.
Nonetheless, malicious actors usually use unlisted extensions to use customers, maintaining them hidden and making it tough for Google to detect. After Tucker started analyzing the 2 suspicious extensions, he uncovered 33 extra. Many connect with the identical servers, use equivalent code patterns, and request the identical permissions.
The apps ask customers for consent to entry delicate information, together with browser tabs and home windows, cookies, storage, scripting, alarms, and administration APIs. This stage of entry is unusually excessive, making it straightforward for unhealthy actors to use the consumer’s system for numerous malicious functions.
“At this level, this info must be sufficient for any group to fairly kick this out of their atmosphere because it presents pointless threat,” Tucker wrote in his weblog on Thursday. “The one permission any of the 35 apps requires is administration,” he added in an email to Ars Technica.
Along with the suspicious variety of permissions these apps request, their programming is equally regarding. Tucker discovered the apps had closely obfuscated code. A developer would solely program their software program this option to make it tough for others to look at and perceive its actions.
Collectively, customers have put in the 35 apps over 4 million instances. Whereas it is unclear how unlisted extensions attracted a lot consideration with out showing in searches, Tucker notes that 10 carried Google’s “Featured” tag – a designation sometimes given to builders Google has vetted and trusts. He did not elaborate on how this will have influenced their distribution.
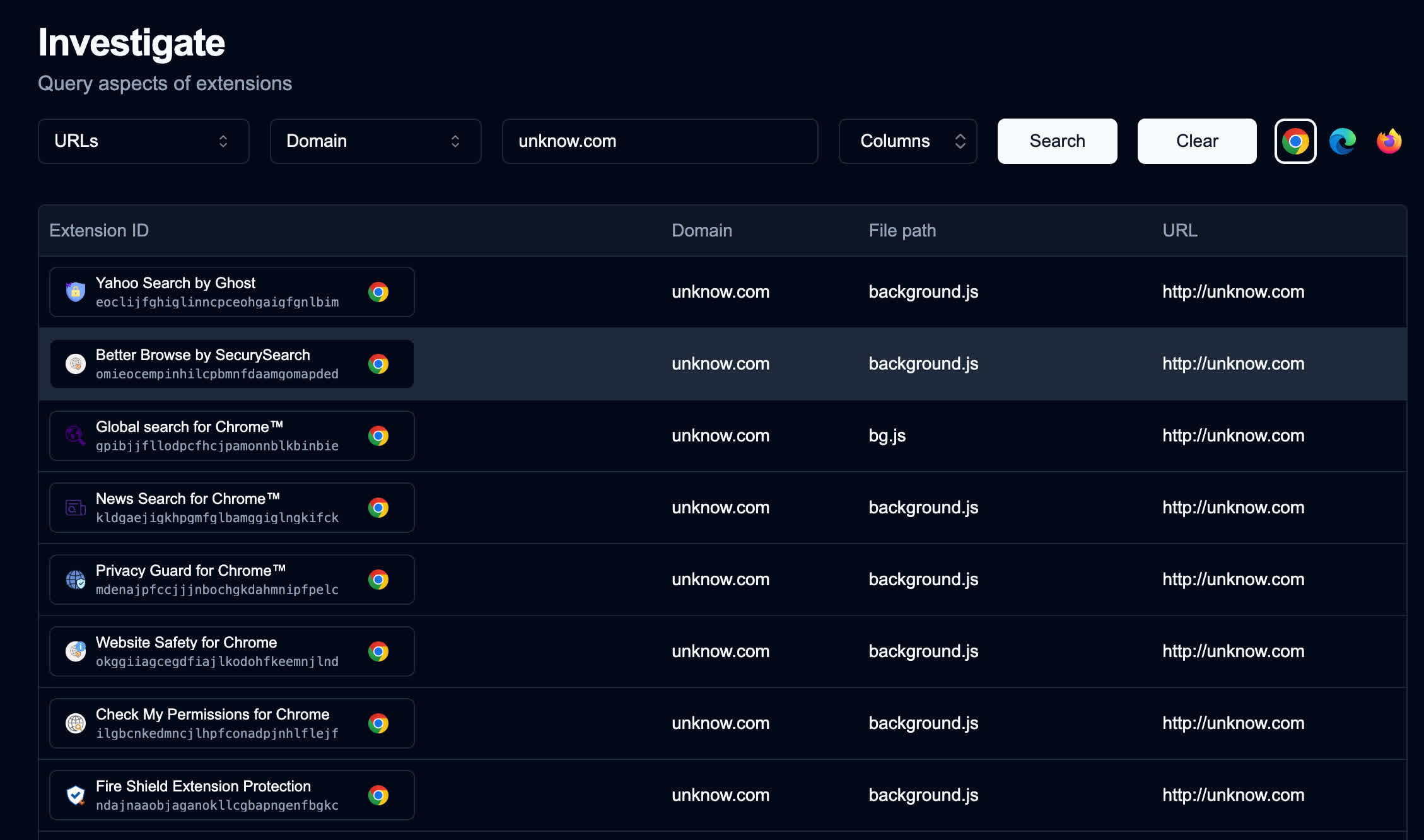
Tucker discovered no direct proof that the extensions exfiltrate information – however that does not rule it out. One software referred to as Hearth Protect Extension Safety paradoxically claims to scan Chrome for malicious or suspicious plugins. After analyzing it, Tucker found a JavaScript file that may add information and obtain code and directions from a number of shady domains, together with one referred to as unknow.com.
This area stands out as a result of all 35 apps reference it of their background service daemons regardless of it having no seen internet presence or clear operate. Whois records record it as “accessible” and “on the market,” making it particularly weird that so many extensions would level to it.
“Hilariously, the area would not have any relevance within the code, however [is] extremely helpful for linking the entire extensions collectively!” Tucker stated.
Safe Annex printed a complete record of extension IDs and permhashes on its weblog and in a publicly accessible spreadsheet. A less complicated record of extension names seems within the picture above. In case you have any of those put in, Tucker recommends eradicating them instantly – the safety dangers far outweigh any potential profit.