Learn extra at:
A sizzling potato: For years, the privateness of Android customers searching the online has been quietly compromised by a complicated monitoring methodology employed by two of the world’s largest tech firms: Meta and Yandex. In accordance with current analysis, each firms have exploited reliable browser-to-app communication protocols to covertly hyperlink nameless net exercise with the identities of customers logged into native apps like Fb, Instagram, and numerous Yandex providers on Android units.
The research, extensively analyzed by Ars Technica, focuses on the widespread use of analytics scripts equivalent to Meta Pixel and Yandex Metrica. These instruments are embedded throughout hundreds of thousands of internet sites, ostensibly to assist advertisers observe marketing campaign efficiency. Nevertheless, behind the scenes, they permit a course of that circumvents the privateness protections constructed into Android and main net browsers.
On the core of the difficulty is the exploitation of Android’s permissive native port communication. Whereas Android’s sandboxing and browser storage partitioning are supposed to maintain net and app information siloed, Meta and Yandex have found strategies to bypass these safeguards, successfully enabling cross-app monitoring.
The trackers ship distinctive net identifiers – equivalent to cookies – by means of native ports monitored by their corresponding apps. This enables Meta and Yandex to hyperlink a person’s searching historical past on to their app account, even when customers are searching in personal or incognito modes.
“What this assault vector permits is to interrupt the sandbox that exists between the cell context and the online context,” Narseo Vallina-Rodriguez, one of many researchers who uncovered the observe, advised Ars Technica. “The channel that exists allowed the Android system to speak what occurs within the browser with the id working within the cell app.”
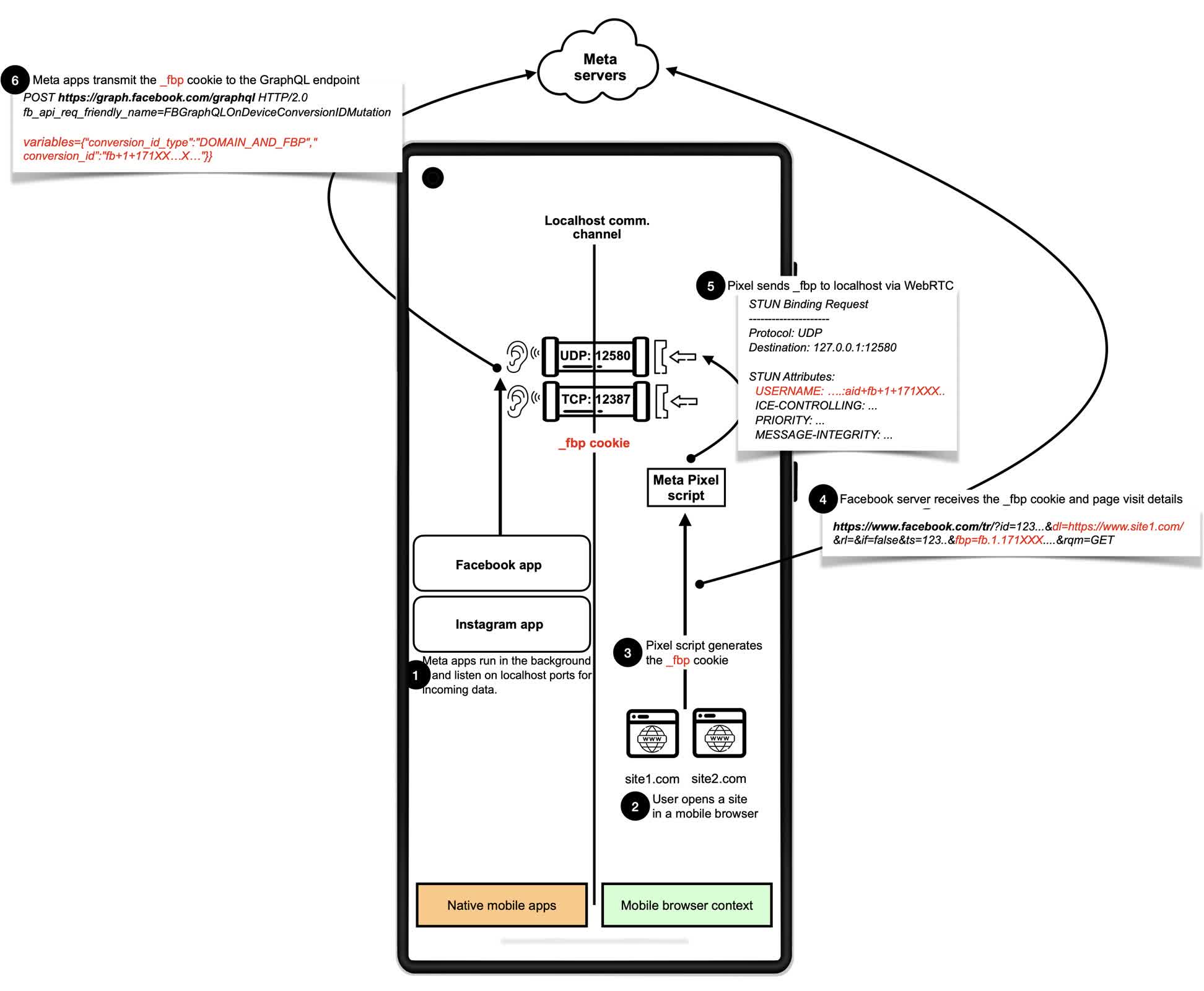
The technical implementation is advanced however revealing. Meta Pixel, for example, has employed a wide range of strategies since September of final yr. Initially, it despatched HTTP requests to port 12387; it later transitioned to utilizing the WebSocket protocol over the identical port.
Later, Meta adopted WebRTC, a protocol usually used for real-time communications like video calls. By manipulating Session Description Protocol SDP information by means of a method often known as SDP munging, Meta Pixel was capable of embed monitoring cookies into fields supposed for connection data. This information was then despatched as a part of a STUN request to the native host, the place the Fb or Instagram app might intercept it and affiliate the exercise with a particular person id.
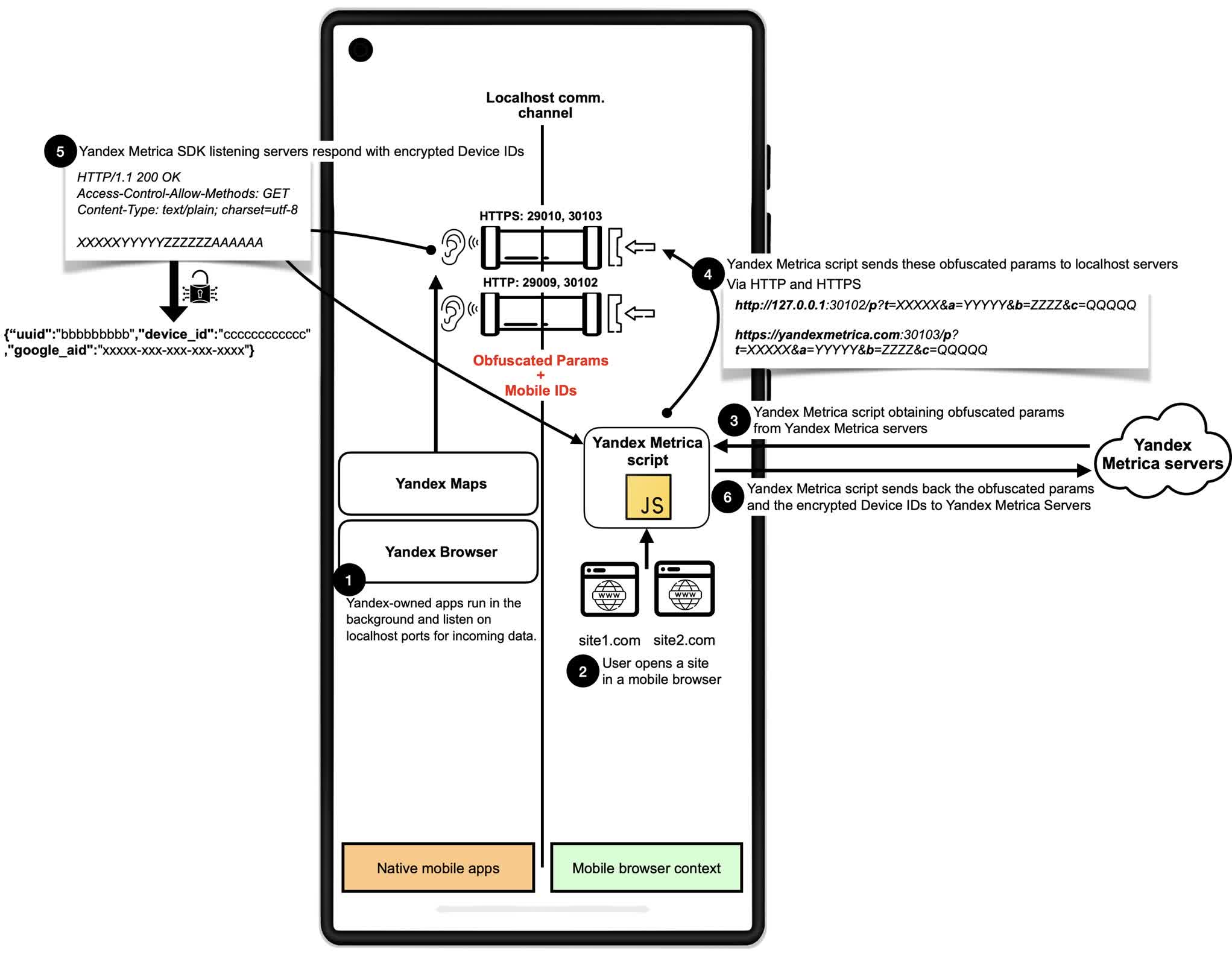
Yandex Metrica has employed related techniques since at the very least 2017, sending HTTP and HTTPS requests to designated native ports monitored by its apps. Each Meta Pixel and Yandex Metrica are estimated to be embedded on hundreds of thousands of internet sites, with Meta Pixel alone discovered on roughly 5.8 million.
Google, the steward of Android, has acknowledged the abuse, stating that it violates each Play Retailer insurance policies and person privateness expectations. “The builders on this report are utilizing capabilities current in lots of browsers throughout iOS and Android in unintended ways in which blatantly violate our safety and privateness rules,” a Google spokesperson stated. The corporate has applied some mitigations and is investigating additional.
Meta, for its half, has paused the characteristic and is at the moment in discussions with Google. “We’re in discussions with Google to handle a possible miscommunication relating to the appliance of their insurance policies. Upon turning into conscious of the issues, we determined to pause the characteristic whereas we work with Google to resolve the difficulty,” based on a press release by the corporate.
Yandex has additionally acknowledged that it’s discontinuing the observe. The corporate claims it doesn’t de-anonymize person information and insists the characteristic was supposed solely to enhance personalization inside its apps.
Some browsers have taken proactive measures. DuckDuckGo and Courageous, for example, have blocked the abusive JavaScript and related domains, stopping identifiers from being despatched to Meta and Yandex.
Vivaldi, one other Chromium-based browser, nonetheless forwards identifiers to native ports except tracker blocking is enabled. Chrome and Firefox have rolled out focused fixes, although researchers warn these are solely partial options that might be bypassed with minor modifications to the trackers’ code.
Gunes Acar, the researcher who first found Meta Pixel’s native port entry, emphasised that the dynamic between browser builders and trackers stays fluid. He described efforts to dam these methods as an ongoing wrestle.
“Any browser doing blocklisting will seemingly enter into a continuing arms race, and it is only a partial resolution. Creating efficient blocklists is difficult, and browser makers might want to consistently monitor the usage of this kind of functionality to detect different hostnames doubtlessly abusing localhost channels after which updating their blocklists accordingly.”